5 Tips to Spots Phishing Emails from a Mile Away
Oct 20, 2021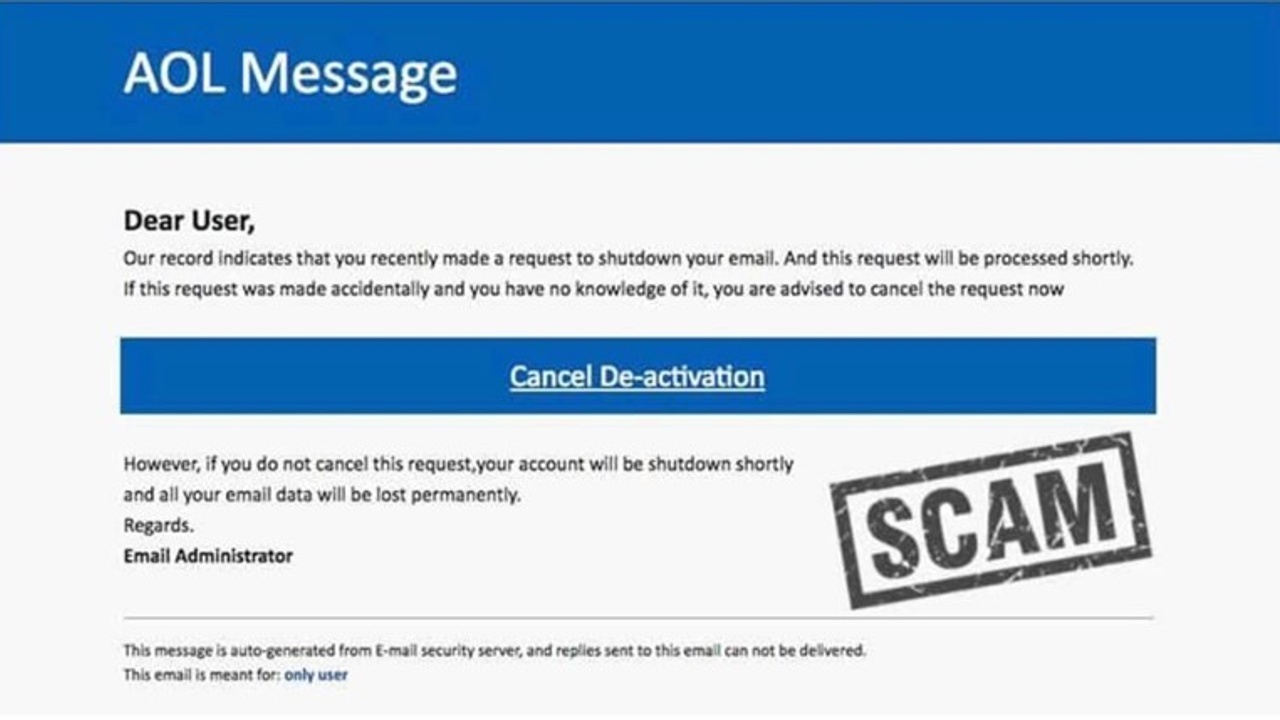
(From hacked.com)
- Beware of Alarming Emails
Hackers don’t want you to think. They want you to act. And there’s no better way to achieve this outcome than to instill panic in a victim.
Phishing emails will often try to get you into your emotions by creating fear. They might appear to be from a legit platform that tells you that you’ve been hacked or that your account will be closed if you don’t act immediately.
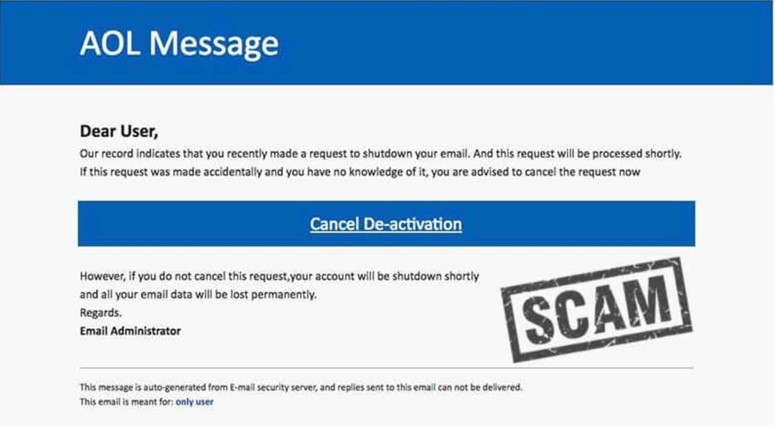
This phishing attempt tried to create panic by threatening cancellation. | Source: Mail Jet
Any time you feel panic from such an email, take a breath and check for the other tell-tale signs of a phisher. Conversely, sometimes these emails are ‘too good to be true.’ They might tell you that you’ve won money and all you need to do is click on their (malicious) link.
- Check For Suspicious Email & Web Addresses
While hackers can create imitation websites that look real, they can rarely create legit email addresses and URLs. Always look at who’s sending the email. It was the best way to spot the recent Instagram copyright infringement scam.
Hackers got people emotionally involved by telling them they infringed on a copyright and that their account would be deleted. They sent it through an email that looked Instagram-official.
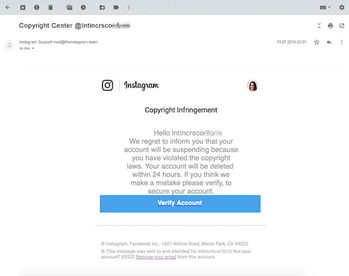
Looks legit, doesn’t it? | Source: Kaspersky
But upon closer examination, you can see it was sent from an email address ending in ‘theinstagram.team’ instead of ‘instagram.com.’
Always make sure the sender is legitimate by checking the email address. And hover over any links before clicking them to be sure they’re real.
- Check for Bad Grammer
Many times, phishing attempts will be riddled with odd language or bad grammar. They might greet you with a word like ‘dear.’
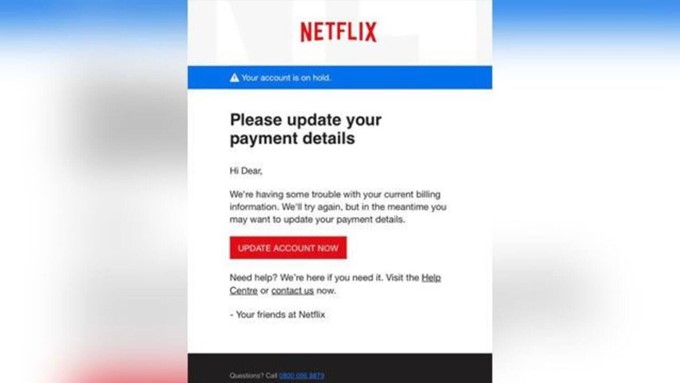
Can you spot the flaws in this real phishing email? | Source: FTC
If something feels off, that’s usually because it is.
- Attachments = Red Flags
Real businesses in 2021 will rarely ask you to download an attachment. If they do, your spidey sense should be tingling. But hackers love attachments. That’s how they can insert malware or ransomware into your computer. Always be suspicious of email attachments, especially ones with extensions commonly associated with malware (.zip, .exe, .scr, etc.).
- Be On the Lookout for Sensitive Data Requests
Be extremely cautious any time a message requests sensitive data from you. Any request for login information or payment information, or personal details should be heavily scrutinized.
If you think the email is actually legit, don’t use any of the communication options provided in the email. Rather, email the company directly with your concerns.
Conclusion
While these tips are a helpful start, they’re only the tip of the iceberg. If you really want to prepare your employees, invest in training and a business protection plan.
Don't miss a beat!
Get regular content, event updates, cybersecurity news and much more delivered straight to your inbox.
We hate SPAM. We will never sell your information, for any reason.

